Ben Chiang
Head of Industrial Ethernet Product Marketing
EtherWAN is committed to providing communication network equipment for mission-critical and large-scale public projects, entering its 24th year this year. From rigorous industrial design, extreme weather applications, high-standard electromagnetic interference and protection, to professional certifications in various special application fields, EtherWAN puts it into place, organizes and analyzes practical needs and transforms them into the best solutions that can help customers solve problems.
Network isolation is always a preferred method in industrial automation and infrastructure projects. In this new era of everything being connected, more than ever has isolation become difficult to manage. Further issues are problems of information efficiency, various cyber security topics, and the fact that hacker and cyber-attacks can no longer be ignored.
In order to have better management experience instead of information blocking, EtherWAN is delighted to announce a plan concerning Safety and Security, and these efforts will be continually invested in order to provide a secure network infrastructure. There are four elements for planning evaluation and assessment.
| Safety | Security | |
|---|---|---|
| Protection conditions from unintentional failure | Conditions for being protected from deliberate human actions or actions | |
| Cybersecurity | Firewall, authority authentication… etc | Hackers...etc |
| Physical Security | CCTV, Access control management...etc | Intruders, burglar...etc |
IEC 62443
The IEC 62443 standard family is divided into four parts, i.e., General, Management System (policies and procedures), Industrial IT Security, IACS (System requirements) and Embedded Security. The components are as shown. EtherWAN, as an industrial networking component manufacturer, is responsible for complying with international requirements to realize system level secure architecture with our partners, mutually sharing the same vision for improved security.
| General | |
|---|---|
| 1-1 | Termininology, concepts and models |
| 1-2 | Master glossary of terms and abbreviations |
| 1-3 | System security compliance metrics |
| Management System | Industrial IT Security, IACS | Embedded Security, Component | |||
|---|---|---|---|---|---|
| 2-1 | Establishing an IACS Security program | 3-1 | Security technologies for IACS | 4-1 | Product development requirements |
| 2-2 | Operating an IACS security program | 3-2 | Security risk assessment and system design | 4-2 | Technical security requirements for IACS components |
| 2-3 | Patch Management in the IACS environment | 3-3 | System security requirements and security levels | ||
| 2-4 | Requirements for IACS solution suppliers | ||||
| Management System | |
|---|---|
| 2-1 | Establishing an IACS Security program |
| 2-2 | Operating an IACS security program |
| 2-3 | Patch Management in the IACS environment |
| 2-4 | Requirements for IACS solution suppliers |
| Industrial IT Security, IACS | |
|---|---|
| 3-1 | Security technologies for IACS |
| 3-2 | Security risk assessment and system design |
| 3-3 | System security requirements and security levels |
| Embedded Security, Component | |
|---|---|
| 4-1 | Product development requirements |
| 4-2 | Technical security requirements for IACS components |
IEC 62443-4-1
Phoenix Contact is the parent company of EtherWAN, and is also one of the first companies to have been certified by TÜV SÜD in accordance with the IEC 62443 series of standards for IT security, Part 4-1:2018 Edition 1.0 (application of the full process profile) in 2018. The central elements of IEC 62443-4-1 are a threat analysis based on the application scenario and a product development process which ensures that all identified security requirements are implemented, verified, and documented with traceability. In addition, device manufacturers must respond appropriately to security vulnerabilities and publish security updates in a reliable manner. EtherWAN Systems, being a group member, will continue the customer-first commitment and expand the idea of IEC62443 spirit to ITS and Energy application sectors.
The statement confirms that EtherWAN's development of secure by design products will be based on a secure development process. This future development emphasizes EtherWAN’s strategy of offering standardized security in products, industry solutions, and consultation services to ensure the future-proof operation of machines, systems, and infrastructures
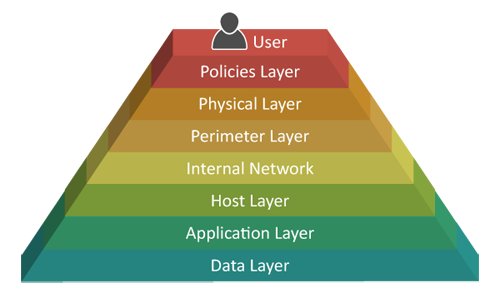
Functional practices
The depth of the defense can be defined as above, and the strategy can be achieved by sophisticated engineers, consultancy, or by contacting EtherWAN for more information. info@etherwan.com.tw
► Cyber Security: 4 Phases of Creating and Maintaining a Secure Industrial Network
The scope of the practices will be extended to IEC 62443-4-2 and more national and industrial safety and security regulations, including the ITS & Energy field. EtherWAN will continue invest and strategically develop solutions to secure your applications and systems, and we welcome partners to join in this task and create a safe & secure system with EtherWAN together.
► IEC 62443 News