Information Technology and Operational Technology
Differences between IT and OT
In order to effectively prevent critical infrastructures and IACS (Industrial Automation and Control Systems) from being invaded and attacked by cyber hackers, causing harm and loss, safety and security considerations and solutions must not only be considered from the perspective of IT, but also from the perspective of OT (Operational Technology).
| Security Policies | IT Network | Security |
|---|---|---|
| Focus | Protect company's business related documents, financial data, IP (Intellectual Property) | Protect human and physical asserts for continuous operations with high efficiency and safety |
| Priorities | 1. Confidentiality 2. Integrity 3. Availability | 1. Availability 2. Integrity 3. Confidentiality |
| Type of Data Traffic | Data, Voice and Video | Data, control information, real time status, safety information |
| Implications of Cyber-attacks | Economic losses, loss of confidential data | Stop processes or services, Physical or environmental damage, endanger the safety or health of personnel |
| Upgrades and Patch Management | During up time, ASAP | Scheduled During Downtime (months, years), ASAP if urgent |
| Infrastructure Life Cycle | Refresh < 5 years | Lifespan 15+ years |
| Deployment Conditions | Controlled and stable environments | Harsh environments |
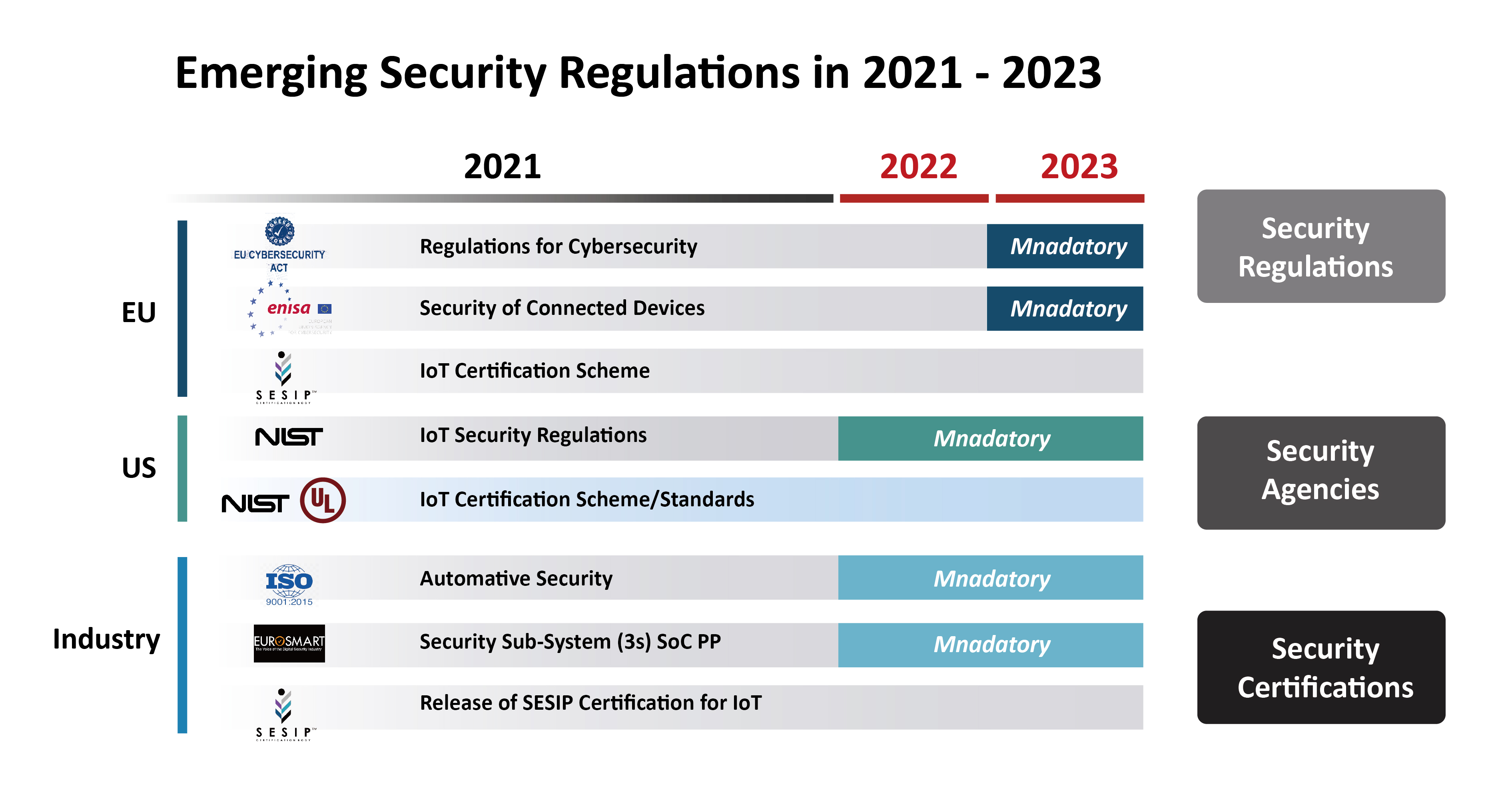
Understanding IEC 62443
IEC 62443 is organized into four parts: General, Policies and Procedures, System, and Component
The "General documents" provide the overall concepts, terminologies, and overview of industrial security.
The "Policies and Procedures" part outlines the requirements and guidelines of establishment of Cyber Security Management System for IACS. The Patch Management for IACS is included in this part as well.
The "System documents" provide the technologies, policy, and risk assessment for designing and implementing security systems.
The "Component" section addresses the requirements of product suppliers and the devices integrated in an IACS solution.
As one of the major industrial network equipment providers, in addition to continuing to providing customers with the best and complete networking solutions, EtherWAN is investing resources and actively working to obtain IEC 62443 certification today. With in-depth understanding and compliance with the IEC 62443 standard to design secure products, EtherWAN will soon provide customers with products and solutions that meet the world's security standards!
Frequently asked questions on Cyber Security
How many types of cyber security are there?
There are many different aspects of cyber security. These include protecting critical infrastructure, applications, networks, the Cloud, IoT and IIoT. Protection is set up not just against unauthorized access, but also sabotage and software-based attacks.
Why is cyber security important?
More connected devices mean more potential threats. If your refrigerator gets hacked, it will be a costly and troublesome problem for you to have fixed. If the operational technology for the local power company is hacked, the problems will be more widespread and dangerous. Cyber security at all levels, from household appliances to industrial control systems must be implemented and constantly adapted to new threats.
What is the IEC 62443 standard?
IEC 62443 is set of standards for cybersecurity in automation and control network systems. Topics are divided into stakeholder and category roles. These roles include operator, service provider, and component manufacturers. Each role is assigned a risk-based approach to activities related to the specific role function.
*View more of Industrial Network Security and IEC 62443 standard .
What is the difference between IoT and cyber security?
The IoT is the background in which cyber security must be implemented. In many instances, this will require both digital and physical steps be taken to secure devices and infrastructure. The exponential growth of the IoT and IIoT has brought security concerns to the forefront in enterprise, educational, and government institutions.
What is IIoT security?
With an ever-increasing number of devices and sensors coming online into the word of IIoT, there is a corresponding increase in the number of access ports, storage media, and communication channels. This has resulted in more potential vulnerabilities to these systems. IIoT security is the securing of devices and data from unauthorized access and other hostile attacks. IIoT is security is broad, protecting against not just hacking, but also malware, sabotage, and other security risks.
What are the IIoT Security Standards?
IIoT Cybersecurity standards are sets of best practices to protect organizations from cyber threats. These standards are wide-ranging, and apply to organizations of all sizes and fields. These IIoT security standards include concepts such as IIoT islands, secure connections, and multi-tenancy.